Today's consumers are exceptionally knowledgeable, which makes you need to prioritize a proactive approach to creating exceptional customer...
Reciprocal Technologies Blog Newsletter • Page 9
6 Critical Considerations for Effective IT Inventory Management
Managing your organization's technology can pose unexpected challenges. Firstly, many businesses overlook their technology as long as it functions...
3 Benefits that Come with a Managed Service Agreement
Technology presents a significant challenge for businesses of all sizes, whether you're a quaint family-run shop or a swiftly expanding enterprise....
AI-Driven Technology is Changing Business
Undoubtedly, AI is becoming a big part of daily life. One can hardly turn on the news without hearing about the latest applications it has, from...
An Automated Backup Eliminates the Guesswork
Gone are the days when businesses relied solely on manual tape backups conducted at specific intervals. Modern solutions like automated backup and...
Let an MSP Revitalize Your Business Technology
We are passionate about showcasing how technology can fuel the growth of businesses, especially small and medium-sized enterprises (SMBs) with...
Three Reasons Why All SMBs Should Encrypt Their Email
Encryption is a powerful tool that any business can use to beef up its security infrastructure. While it’s often discussed in the context of virtual...
Automation Can Help SMBs Improve Their Business
Automation has been a hot-button issue in business for a while. Lots of businesses are looking to automate several different areas of their...
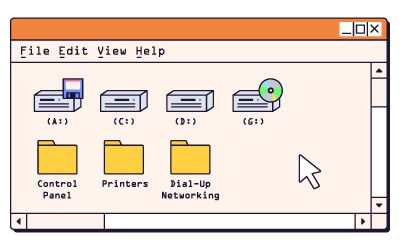
Unpacking the Type of Drives on Your PC
When discussing technology, the term "drives" is frequently used. This term encompasses various types that a computer may utilize in its daily...
Cybersecurity Training Can Be a Bore, but It Doesn’t Have to Be
Cybersecurity training can be an overwhelmingly annoying issue for everyone. Unfortunately, it’s a must. Understanding the reasons behind this...